TL;DR

Estimated reading time: 4 minutesAdvanced EXE multi protection against reverse engineering by free toolsHello Cybrarians,This essay is about protecting .exe files against reverse engineering and making it harder for crackers to unpack and crack our .exe files. We are going to use free tools for this purpose but this time we use them in a tricky way. To be honest, I must say that if someone claims that my program is protected in a way that no one can crack it, he is completely wrong. Each program that can be run in an operating system can be cracked by some means. So, all we can do is to make it harder for crackers and reverse engineers to decompile our program.I am going to use a sample .exe called Autoruns from Microsoft.

This file is a useful .exe written in Microsoft visual c++ and we use it as our sample .exe. We need these tools as well. You can download them here:
- A powerful packer identifier and useful EXE scanner called DIE (Detect It Easy)

- Another famous EXE Identifier called ExeInfoPE

- The powerful free UPX .exe packer
- A very useful tool for reverse engineers called Explorer Suite (CFF Explorer) from NTCore

- The Enigma Virtual Box from enigmaprotector.com which is a freeware used for file system virtualization and allows you to consolidate all files used by your application into a single executable file without having to extract virtual files to the disk. It packs the files too.

Now that we have all tools installed let us start protecting our EXE file:
Open Autoruns.exe file in cff explorer. We want to pack our .exe file with UPX packer but modify it manually in some ways in order to defeat unpacking it simply with UPX –d switch or any automated UPX unpacker.

Now click on UPX Utility and we have this.

Simply click on Pack button at right pane.

And go to the file menu and click on Save as.

Save the new packed file with an optional name. [I saved it as Autoruns_packed.exe]
Now open the new packed file (Autoruns_packed.exe) in CFF Explorer again, and this time click on Section Headers.

We have new sections in our PE Header and it says that we used UPX. Open Autoruns_packed.exe in DIE (Detect it easy ) and we see that it detects the packer as UPX.

Your UPX version may be different than mine, as I have substituted the new version of UPX.exe v3.93 in the “C:Program FilesNTCoreExplorer SuiteExtensionsCFF ExplorerUPX Utility” and updated my upx.exe in CFF Explorer.
If we check our Autoruns_packed.exe in ExeInfoPE we get this.

And again it says that our .exe is packed with UPX ver 3.93.
Since we want a modified UPX version in order to be difficult to unpack, we do the following things:
Reopen Autoruns_packed.exe in CFF Explorer and go to Section Headers. Double click on UPX0 in the right pane under Name section and change it to whatever name you want. I changed it to code8. Do this for the two other sections:
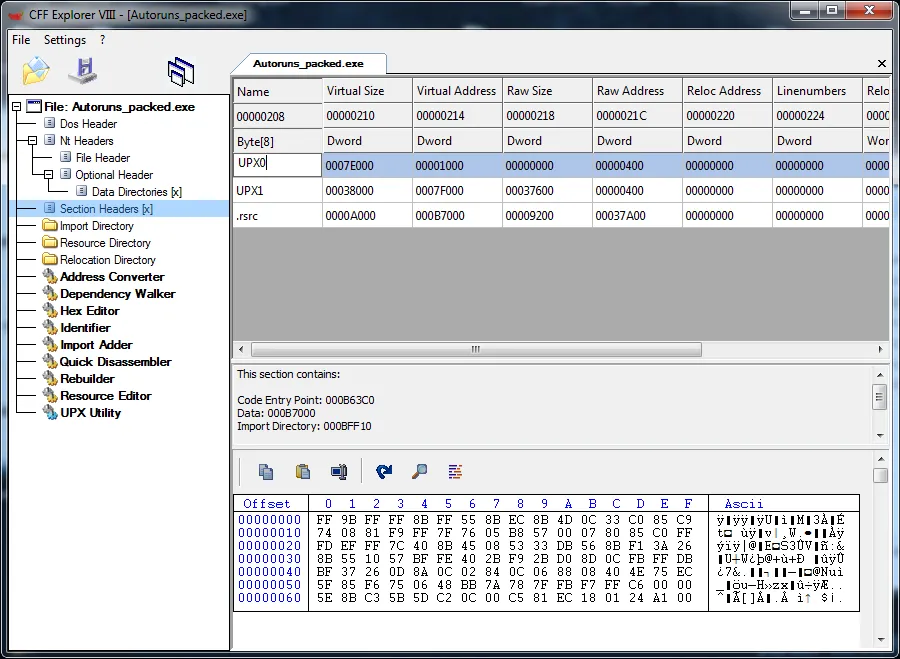
And we have this.

Now click on Hex Editor in the left pane and scroll down the mouse at right pane until you see this:

Change it to whatever you want but it is better not to exceed the amounts of characters(change until!) like this:

Now click File menu and save and confirm to save.

Reopen Autoruns_packed.exe in Detect it easy program and we have

Bingo ; ) A modified UPX version that can not easily be unpacked with upx –d or any other automated upx unpacker. Let us check it with ExeInfoPE:

This one also says it is a modified version. Now let's check it to see if we can unpack it with UPX.

UPX could not unpack our file. But have we done. Not yet. Let us make it harder to unpack again. Oper Autoruns_packed.exe in Enigma Virtual Box installed on your computer:

And click on Files Options -> check compress files
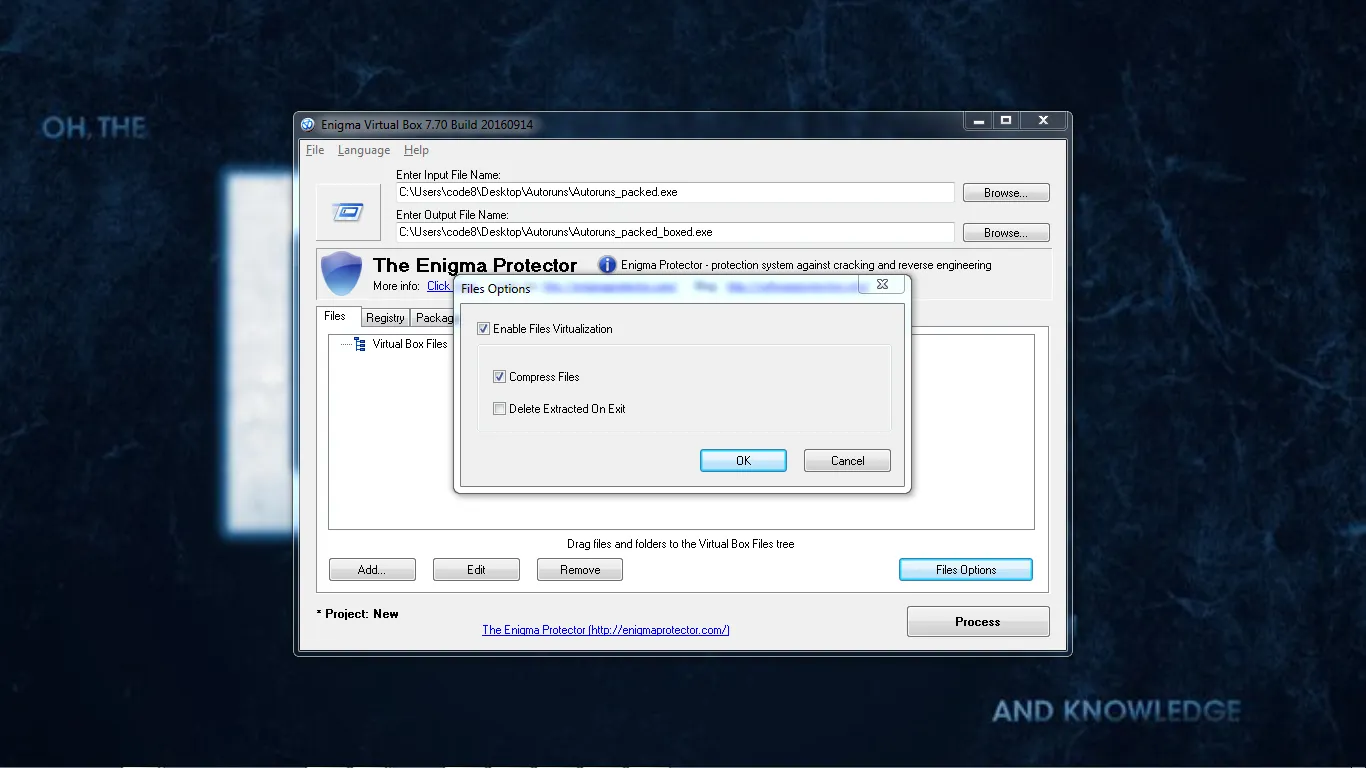
Click on OK and Process and -

Congratulations! You have just passed level 2 protection of your EXE.Let us check to see what is detected by our packer detectors?
With Detect it's an easy extra protector is detected:

And in ExeInfoPE:

Enigma is detected but there is not ant footprint of UPX.
Wait, what if I change the section headers again in CFF Explorer. I love to try new ways. ;)
So let us change the sections. Open our new Autoruns_packed_boxed.exe in CFF Explorer . Now we have two extra sections called an enigma. Let us change it to code8 and see what happens again.


I changed it and saved as Autoruns_packed_boxed_modified.exe. Have a look to our packer detectors again and we have:

Ohhh! Enigma has gone and now we have just a UPX modified version. That is excellent as we have a hidden layer of protection that is very hard to guess or find.
And in ExeInfoPE:

Just the same. Oh, I forgot to say run the program to see if it runs or not. |-_-|
The program works perfectly! ;) And this method can be used in 99% of software and exe files.
Thanks for reading.





