TL;DR
This post covers CUPP (The Common User Password Profiler), which is a wordlist generator. It can be used to generate custom wordlists for the red team and pentesting engagements.
About CUPP
CUPP is a powerful tool for generating a wordlist for brute force attacks. It's written in Python and hence cross-compatible with almost any platform capable of running Python scripts. To run, CUPP needs data about the target (their name, wife's name, pet's name, phone number, and so on), and it then generates passwords based on the keywords entered.
How does CUPP work?
People tend to show some patterns when it comes to choosing passwords. They usually pick passwords that are easy to remember and include personal things into their passwords. For example, to easily remember a password, it can contain someone's birthday or the name of their husband/wife. If their wife's name is Lucy, whose birth date is 05/07/1978, they may have a password similar to "Lucy05071978". CUPP uses an algorithm to predict these passwords based on the target's data to generate a very effective wordlist for credential brute-forcing. Hence, it's pretty useful for red teaming and pentesting engagements where password spraying and credential stuffing are in scope.
Steps:
1. Installing and setting up CUPP in Kali Linux
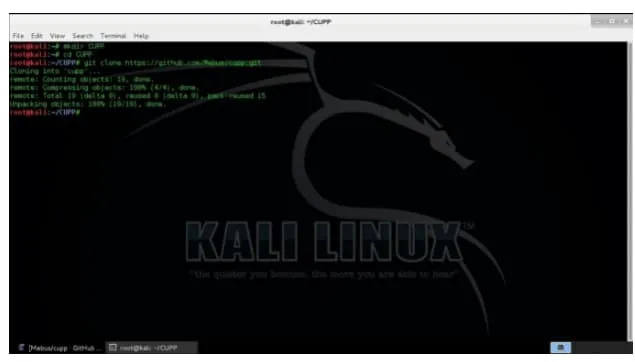
The first and most important step is installing CUPP on Kali. After booting to Kali Linux, open the terminal and create a directory for installing the CUPP tool.
Use the following command:
mkdir CUPP
This command creates a folder or directory where the files for the tool will be stored.
Navigate to this newly created directory:
cd CUPP
Inside the CUPP directory, clone the CUPP repository from Github:
git clone https://github.com/Mebus/cupp.git
If git doesn't work, it might not have been properly installed in the system. If so, use the command to update the sources and install it again: apt-get update && apt-get install git
2. Configuring CUPP after Installation
Like a lot of hacking tools, CUPP, too, has a configuration file. Let's explore and customize its options. When the ls command is used after cloning CUPP, one can see that a new folder named "cupp" is created. Upon navigating to that folder, the config file should be visible:
cupp.config
The CUPP documentation is available in the README.md file inside the directory cloned with git.
Open the configuration with leafpad:
leafpad cupp.cfg
This opens a screen with many options:
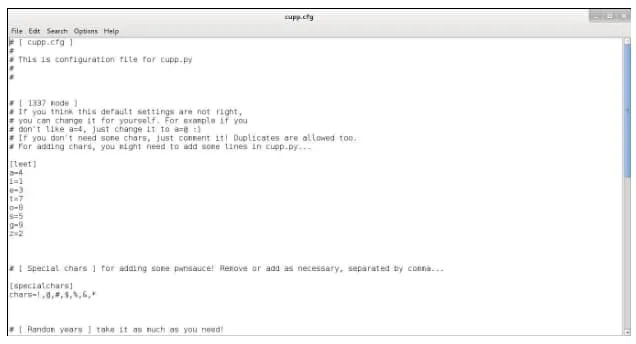
For now, let's focus on the "1337 mode" and special chars settings. What 1337 mode does is simply going through all the passwords CUPP generated and replacing, for example, "a" with 4 in that password and adding the new password to the wordlist. This mode not only makes the wordlist larger but also greatly increases the chances of success. Note that a should be equal to "@" as well.
To do that, add this line under "leet": a=@
Special characters will be added randomly at the end of the passwords which CUPP generates. These need not be edited, but if one wants to, it can be done by adding a character to it. The other settings are quite self-explanatory.
3. Using CUPP
CUPP can be launched in interactive mode by using the following command: python cupp.py -i
Enter all the information and particulars about the target. This information can be gained through OSINT research about the target. As an example, the imaginary "target" here will be John Smith.
Knowing about the target is important. In this case, one must collect details about John to effectively generate wordlists using CUPP. For this example, let's assume that John:
- Is an electrician by profession.
- Was born 05/10/1987.
- Often Goes by the nickname "Tirrian"
- Has a wife named Barbara, but her nickname isn't known.
- His wife's birth date is 14/07/1989.
- Has a son named Alex, whose nickname is unknown. His son was born on 19/03/2005.
- Has a dog named Laika.
- Owns a company named ElectricFab (a fictitious company for this writeup)
- Is a huge soccer fan and supporter of Real Madrid.
Let's also assume John included barbara in his password, which is easy to remember, but replaced the a's with @'s to make it more secure. He further added the birthday of his wife, which is 14/07 but omitted the dashes. So, his password is mostly a combination of known information about him: B@rb@r@1407.
Note: This password contains a capital letter, is 8 characters long, has a number in it, and has a special character, which meets the minimum password complexity requirements on most sites. (John Smith is an imaginary person with no relation to anyone in real life)
Upon checking if CUPP can predict this password from the given data, it generated a dictionary of 37,000 possible passwords for John, called John.txt.
4. Using a Test case to determine if CUPP generates the password successfully
To check whether CUPP successfully generated John's password, one can use leafpad to open the text file:
leafpad John.txt
Once it's opened, click "search" and click on "find." Then, enter John's password.
Or,
Grep through the contents of the text file containing generated passwords like this:
cat John.txt | grep 'B@rb@r@1407'
Grep would highlight the portion of the wordlist where it found a match. Thus, CUPP's wordlist generation capabilities are quite advanced and powerful, as demonstrated through this simple example.
Defense against Password Spraying and Brute Force attacks
Don't use easily memorable passwords. Generate passwords through password managers like Lastpass and 1password, which make it hard to determine for attackers.
Easier to remember passwords are always easier to crack, as was demonstrated in this test case
Use password managers to set up stronger passwords that are harder to crack and stored securely. Password managers also have an added advantage of ease of use because one doesn't need to remember them. Most password managers have an auto-fill mechanism that fills the password on the right website without manually entering them.
To stay up-to-date and aware of such cyber risks, and learn about more hacking tools, consider signing up to Cybrary by clicking on the Sign-Up button on the top right corner of the page.





