TL;DR

The Microsoft System Center Configuration Manager, or SCCM, has seven reports that you can use to help manage your Microsoft Endpoint Protection software. From an Overall Status and History to Top User Threat List, you can usually get what you need. In some cases though, you may have to dig into a few reports, export the data to an Excel sheet, and then start combining this data just to get some basic details.Here, I am going to show you a couple of PowerShell scripts that will help you manage your Endpoint Protection software at a glance.The first script, Endpoint Protection Status, will give you a quick overview of a machine and whether or not it’s up to date, the last scan run, the last infection found, if any, and the results of that infection. (Editor’s Note: All scripts provided are as is. They are written to allow you to cycle through computers instead of running the script separately on each computer.)
EndPointProtectionStatusCheck.ps1
The status of a machine’s security software is vital, and it needs to be known immediately. Without digging through reports or waiting for SCCM to load, this PowerShell script will do that.This is the general output for a non-infected machine and an infected machine. All data was retrieved in under 30 seconds.
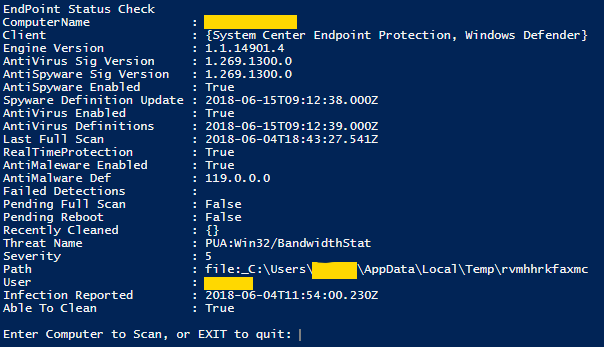
The PowerShell Script:
`Clear-Hostwhile (1 -ne 2){$Computer = $Null$OS = $Null$Computer = Read-Host "Enter Computer to Scan, or EXIT to quit"Write-Host ""if ($Computer -eq "EXIT") {exit;}if(Test-Connection -ComputerName $Computer -Count 1 -Quiet -WarningAction SilentlyContinue -ErrorAction SilentlyContinue){$PCHEALTH = Get-WmiObject -Query "select * from AntiMalwareHealthStatus" -Namespace "rootMicrosoftSecurityClient" -ComputerName $Computer | Select-Object PSComputerName,AntispywareEnabled,AntispywareSignatureUpdateDateTime,AntivirusEnabled,AntivirusSignatureUpdateDateTime,LastFullScanDateTimeEnd,RtpEnabled,NisEnabled,NisSignatureVersion,Version, AntispywareSignatureVersion, AntiVirusSignatureVersion, EngineVersion$PCINFSTAT = Get-WmiObject -Query "select * from AntiMalwareInfectionStatus" -Namespace "rootMicrosoftSecurityClient" -ComputerName $Computer | Select-Object CriticallyFailedDetections,PendingFullScan,PendingReboot,RecentlyCleanedDetections$PCDETECTION = Get-WmiObject -Query "select * from Malware" -Namespace "rootMicrosoftSecurityClient" -ComputerName $Computer | Select-Object ThreatName,path, SeverityID, User,DetectionTime,ActionSuccess$Client = Get-WmiObject -Query "select * from AntiVirusProduct" -Namespace "rootSecurityCenter2" -ComputerName $ComputerWrite-Host "EndPoint Status Check"$Object = New-Object PSObject -Property ([ordered]@{ComputerName = $PCHEALTH.PSComputerNameClient = $Client.displayname"Engine Version" = $PCHEALTH.EngineVersion"AntiVirus Sig Version" = $PCHEALTH.AntiVirusSignatureVersion"AntiSpyware Sig Version" = $PCHEALTH.AntispywareSignatureVersion"AntiSpyware Enabled" = $PCHEALTH.AntispywareEnabled"Spyware Definition Update" = $PCHealth.AntispywareSignatureUpdateDateTime"AntiVirus Enabled" = $PCHealth.AntivirusEnabled"AntiVirus Definitions" =$PCHealth.AntivirusSignatureUpdateDateTime"Last Full Scan" = $PCHealth.LastFullScanDateTimeEnd"RealTimeProtection" = $PCHealth.RtpEnabled"AntiMaleware Enabled" = $PCHealth.NisEnabled"AntiMalware Def" = $PCHealth.NisSignatureVersion"Failed Detections" = $PCINFSTAT.CriticallyFailedDetections -join "`n""Pending Full Scan" = $PCINFSTAT.PendingFullScan"Pending Reboot" = $PCINFSTAT.PendingReboot"Recently Cleaned" = $PCINFSTAT.RecentlyCleanedDetections"Threat Name" = $PCDETECTION.ThreatName -join "`n""Severity" = $PCDETECTION.SeverityID"Path" = $PCDETECTION.Path -join "`n""User" = $PCDETECTION.User -join "`n""Infection Reported" = $PCDETECTION.DetectionTime -join "`n""Able To Clean" = $PCDETECTION.ActionSuccess} )Write-Output $Object} else {Write-Host "$Computer is not online.`n";continue}}`Forcing a machine to update its Endpoint Protection or starting a scan can be managed with PowerShell too. Here are the scripts used. Both will provide a PID number in the terminal once the process has started.With the PowerShell command line scan, you have the option to do a Quick Scan, Full Scan, or Custom Scan. Just change the line in the code. Both of these two scripts utilize Sysinternals PSExec, which can be downloaded from Microsoft.
Endpoint Force Scan
`Clear-Hostwhile (1 -ne 2){$Computer = $Null$OS = $Null$Computer = Read-Host "Enter Computer to Scan, or EXIT to quit"if ($Computer -eq "EXIT") {exit;}Write-Host ""Write-Host "Checking if computer is online..."If (test-connection -count 1 -ComputerName $computer -Quiet) {$OS = gwmi win32_operatingsystem -ComputerName $computer | % caption }if ($OS -eq $Null){Write-Host "Machine Offline"}elseif ($OS -like "*Win*10*"){Write-Host "Windows 10 - Host Online"PSexec.exe -s -h -d \$Computer -accepteula "$($env:programfiles)Windows DefenderMpCmdRun.exe" -Scan -ScanType 2Wait-Event -Timeout 15}elseif ($OS -like "*Win*7*"){Write-Host "Windows 7 - Host Online"PSexec.exe -s -h -d \$Computer -accepteula "$($env:programfiles)Microsoft Security ClientMpCmdRun.exe" -Scan -ScanType 2Wait-Event -Timeout 15}} else{Clear-Hostcontinue}`
Endpoint Force Update (Combined Script with Endpoint Status Script)
`Clear-Hostwhile (1 -ne 2){$Computer = $Null$OS = $Null$Computer = Read-Host "Enter Computer to Update, or EXIT to quit"if ($Computer -eq "EXIT") {exit;}Write-Host ""Write-Host "Checking if computer is online..."If (test-connection -count 1 -ComputerName $computer -Quiet) {$OS = gwmi win32_operatingsystem -ComputerName $computer | % caption }if ($OS -eq $Null){Write-Host "Machine Offline"}elseif ($OS -like "*Win*10*"){Write-Host "Windows 10 - Host Online"PSexec.exe -s -h -d \$Computer -accepteula "$($env:programfiles)Windows DefenderMpCmdRun.exe" -removedefinitions -dynamicsignaturesWrite-Host "Removing old definitions"Wait-Event -Timeout 10PSexec.exe -s -h -d \$Computer -accepteula "$($env:programfiles)Windows DefenderMpCmdRun.exe" -SignatureUpdateWrite-Host "Forcing definition update"Wait-Event -Timeout 15}elseif ($OS -like "*Win*7*"){Write-Host "Windows 7 - Host Online"PSexec.exe -s -h -d \$Computer -accepteula "$($env:programfiles)Windows DefenderMpCmdRun.exe" -removedefinitions -dynamicsignaturesWrite-Host "Removing old definitions"Wait-Event -Timeout 10PSexec.exe -s -h -d \$Computer -accepteula "$($env:programfiles)Microsoft Security ClientMpCmdRun.exe" -SignatureUpdateWrite-Host "Forcing definition update"Wait-Event -Timeout 15}$PCHEALTH = Get-WmiObject -Query "select * from AntiMalwareHealthStatus" -Namespace "rootMicrosoftSecurityClient" -ComputerName $Computer | Select-Object PSComputerName,AntispywareEnabled,AntispywareSignatureUpdateDateTime,AntivirusEnabled,AntivirusSignatureUpdateDateTime,LastFullScanDateTimeEnd,RtpEnabled,NisEnabled,NisSignatureVersion,Version, AntispywareSignatureVersion, AntiVirusSignatureVersion, EngineVersion$PCINFSTAT = Get-WmiObject -Query "select * from AntiMalwareInfectionStatus" -Namespace "rootMicrosoftSecurityClient" -ComputerName $Computer | Select-Object CriticallyFailedDetections,PendingFullScan,PendingReboot,RecentlyCleanedDetections$PCDETECTION = Get-WmiObject -Query "select * from Malware" -Namespace "rootMicrosoftSecurityClient" -ComputerName $Computer | Select-Object ThreatName,path, SeverityID, User,DetectionTime,ActionSuccess$Client = Get-WmiObject -Query "select * from AntiVirusProduct" -Namespace "rootSecurityCenter2" -ComputerName $Computer$Object = New-Object PSObject -Property ([ordered]@{ComputerName = $PCHEALTH.PSComputerNameClient = $Client.displayname"Engine Version" = $PCHEALTH.EngineVersion"AntiVirus Sig Version" = $PCHEALTH.AntiVirusSignatureVersion"AntiSpyware Sig Version" = $PCHEALTH.AntispywareSignatureVersion"AntiSpyware Enabled" = $PCHEALTH.AntispywareEnabled"Spyware Definition Update" = $PCHealth.AntispywareSignatureUpdateDateTime"AntiVirus Enabled" = $PCHealth.AntivirusEnabled"AntiVirus Definitions" =$PCHealth.AntivirusSignatureUpdateDateTime"Last Full Scan" = $PCHealth.LastFullScanDateTimeEnd"RealTimeProtection" = $PCHealth.RtpEnabled"AntiMaleware Enabled" = $PCHealth.NisEnabled"AntiMalware Def" = $PCHealth.NisSignatureVersion"Failed Detections" = $PCINFSTAT.CriticallyFailedDetections -join "`n""Pending Full Scan" = $PCINFSTAT.PendingFullScan"Pending Reboot" = $PCINFSTAT.PendingReboot"Recently Cleaned" = $PCINFSTAT.RecentlyCleanedDetections"Threat Name" = $PCDETECTION.ThreatName -join "`n""Severity" = $PCDETECTION.SeverityID"Path" = $PCDETECTION.Path -join "`n""User" = $PCDETECTION.User -join "`n""Infection Reported" = $PCDETECTION.DetectionTime -join "`n""Able To Clean" = $PCDETECTION.ActionSuccess} )Write-Output $Object} else{Clear-Hostcontinue} `
Conclusion
This is by no means an “End All” to managing your machines. But it is very useful and helpful in a pinch. You should still be checking your reports on a regular basis as well.





