TL;DR
Burp Suite acts as a proxy that allows pentesters to intercept HTTP requests and responses from websites. Not just web applications, the Burp Proxy is capable of proxying through requests from almost any application like Thick Clients, Android apps, or iOS apps, regardless of what device the web app is running on if it can be configured to work with a network proxy. However, Burp Suite may need some tweaking, depending on the network configuration of the application.
This series primarily focuses on the core features of Burp Suite, from the basics to an in-depth overview of maximizing productivity in penetration tests using Burp Suite. In this part of the series, some useful features of the Burp Proxy are explained.
The Burp Proxy
Burp Proxy is a core feature of Burp Suite. It’s a very powerful utility within Burp Suite that can be used to intercept HTTP requests from websites proxied through Burp, modify them, and pass them over to the target server. It allows one to look for security vulnerabilities in the application by simulating the steps an attacker might take to modify and tamper requests going to the server.
Purpose To capture, modify, and control requests originating from Web Applications.
Setting up the Burp Proxy (Configuration) Burp’s embedded browser comes pre-configured, needs no proxy settings, and can be launched by clicking on Open Browser. However, other (external) browsers need to be configured to work properly with the Burp Proxy as described below.
Assuming one has installed Burp Suite already, to use the Proxy tool, the browser proxy settings need to be configured to match the Burp suite proxy listener port (usually, port 8080 by default), and toggle the “Intercept” button to ON state, so that Burp starts intercepting the requests in Proxy.
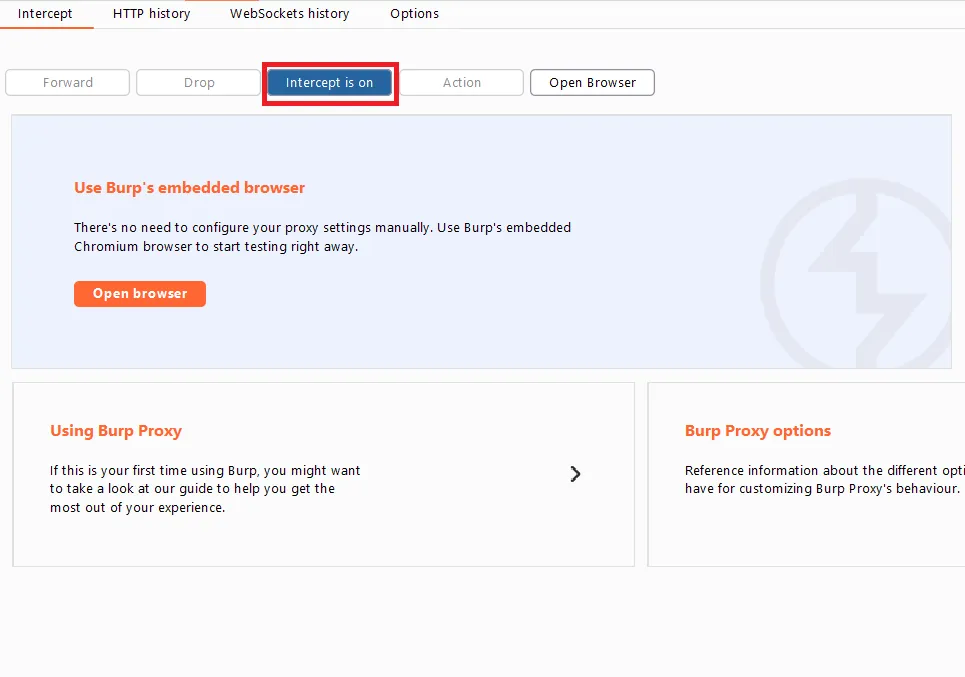
Also, to intercept HTTPS requests, to avoid browser SSL errors, the Burp CA certificate needs to be installed by visiting http://burpsuite in the browser (to download it) and then importing it to Trusted Root Certificate Authorities in the browser Manage certificates settings.
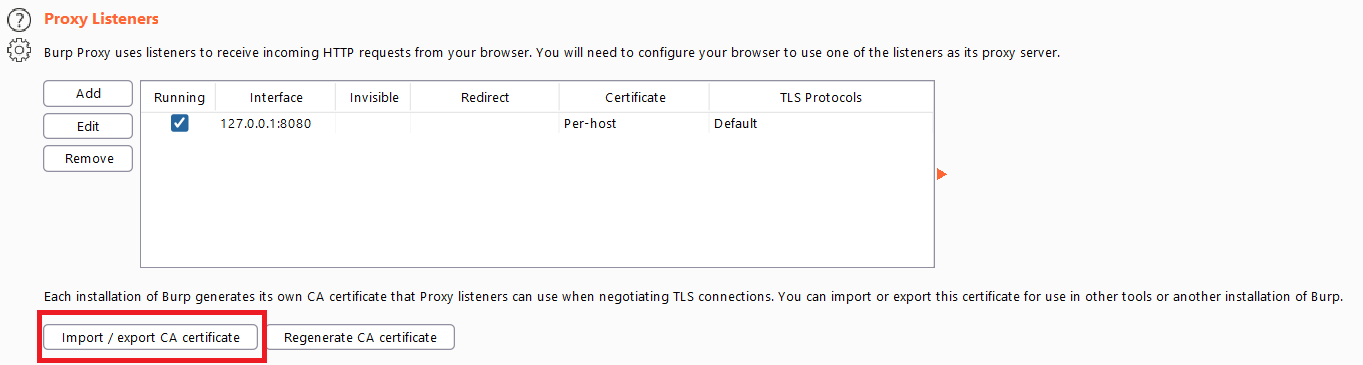
The certificate can be downloaded directly from the Burp Proxy Options tab using the certificate Export feature after clicking on the import/export CA certificate in the Proxy Listeners section.
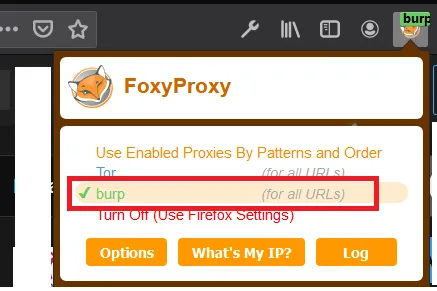
Managing Browser Proxy Profiles using FoxyProxy for more productivity Proxy settings in the browser can be managed using a browser extension like FoxyProxy, which allows switching between proxy profiles in the browser easily. For example, if one needs to use several proxies, it becomes quite useful to switch between the Burp Proxy and resume normal browsing by turning it off or choosing another proxy.
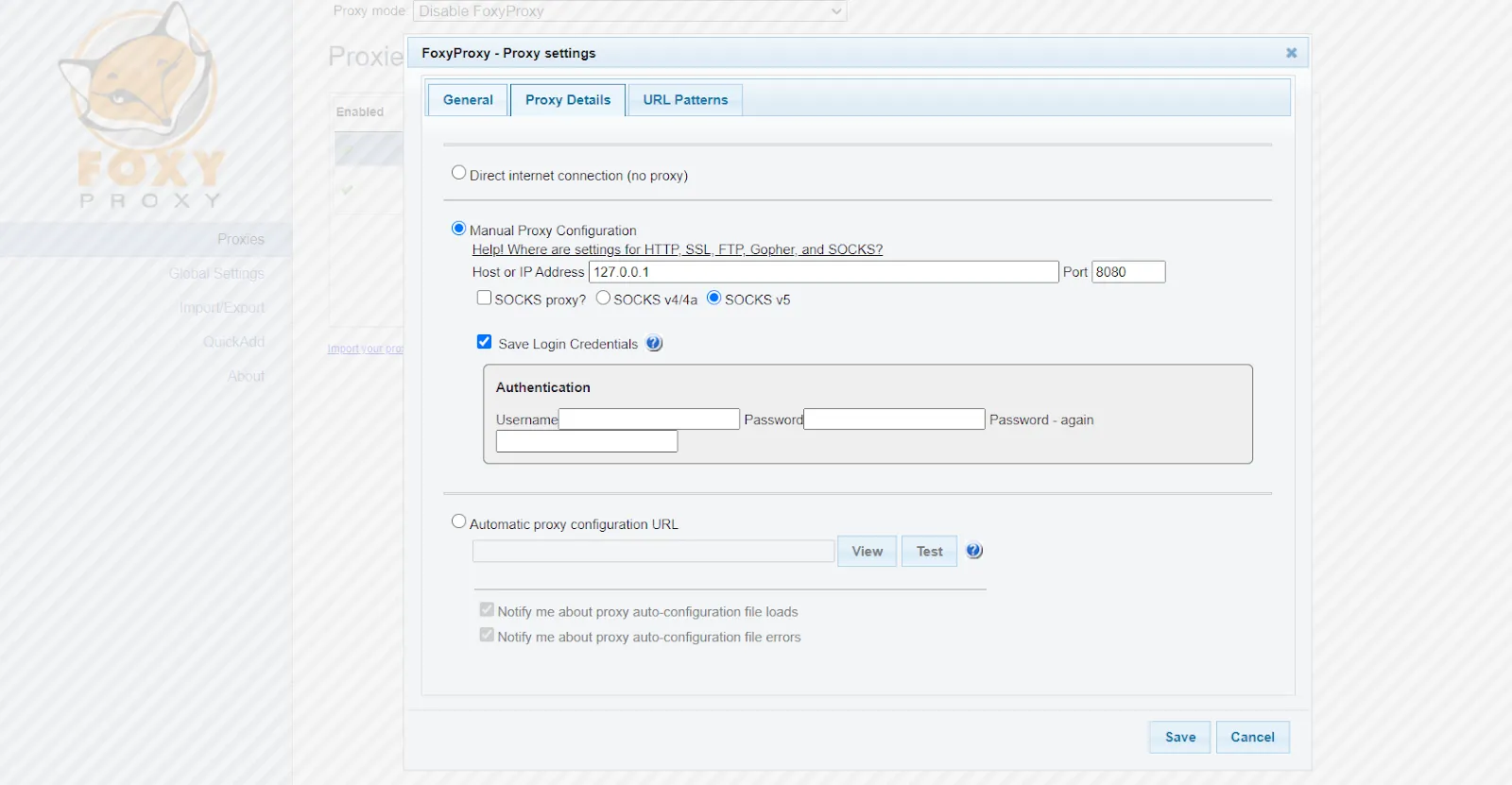
Before using FoxyProxy, one needs to set up the Burp Proxy in FoxyProxy by clicking on Options, and then Add New Proxy with the following settings in the Proxy Details tab.
After setting up the Burp Proxy and intercepting a request from the browser, one can perform several actions on it that are discussed below.
Main Features of Burp Proxy
Out of the box, the proxy tool comes with many built-in features, but only the main functionalities are discussed here.
Intercepting Requests This is the main feature of the Burp Proxy, and after setting it up, the very first tab in the Proxy tool is the Intercept (or, Interceptor) that captures, or intercepts, requests from the browser, sent by web applications or websites running in the browser, to perform further actions on them.
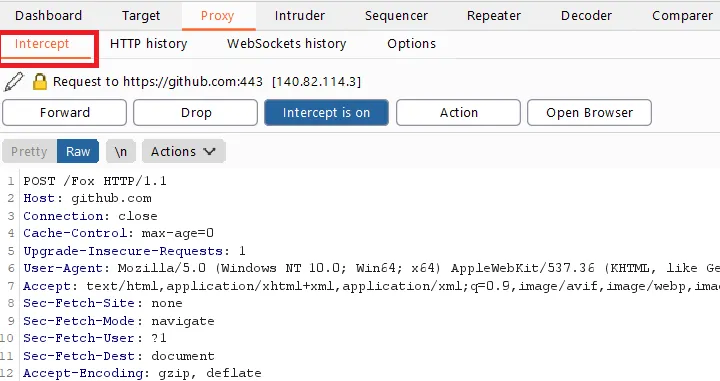
Intercepting Response to Requests Responses from the server for Forwarded Requests can also be intercepted in the Burp Proxy, as shown below. Also, one can modify the server response to test for bypassing frontend checks in the application or to check application behavior upon changing server response.
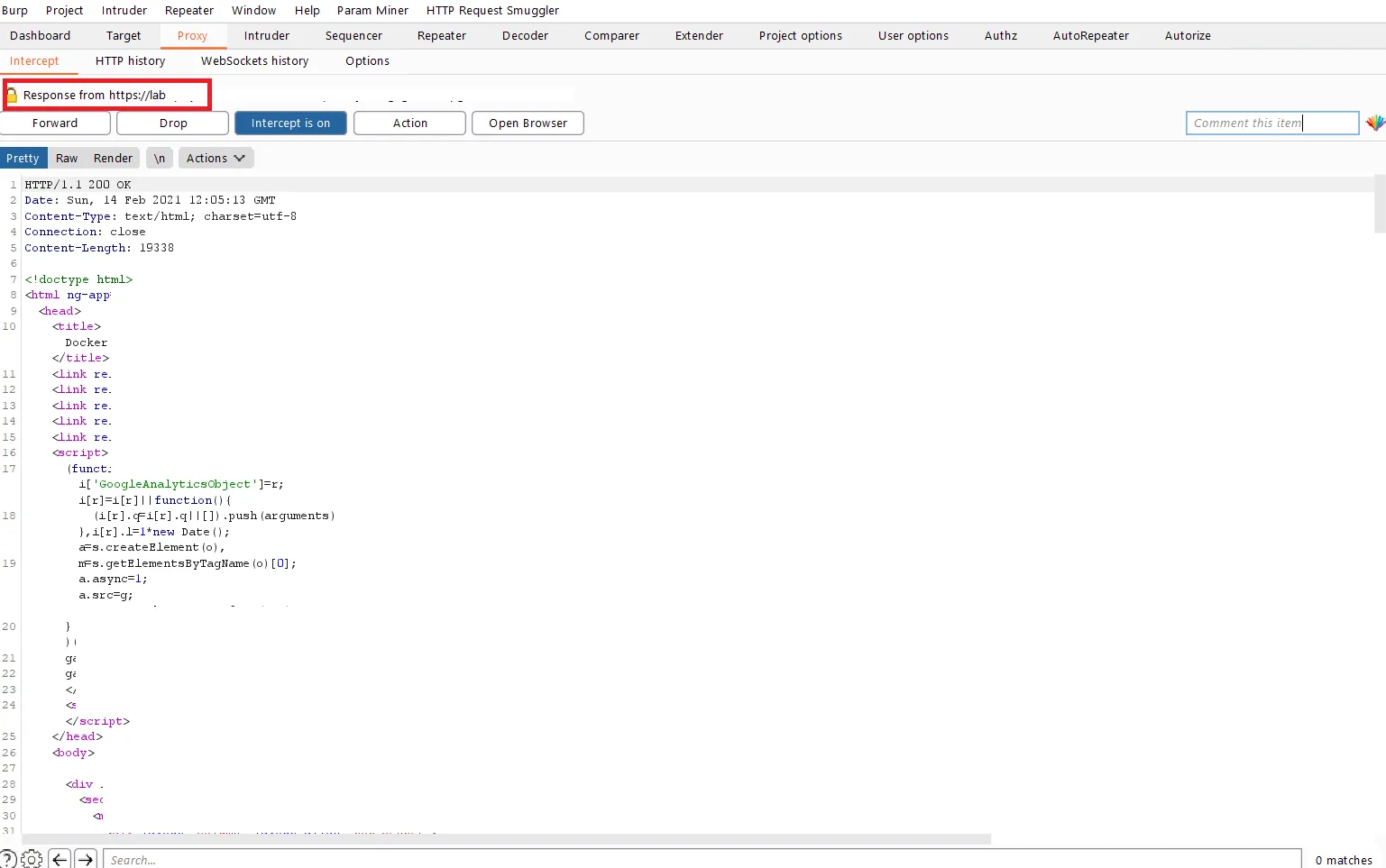
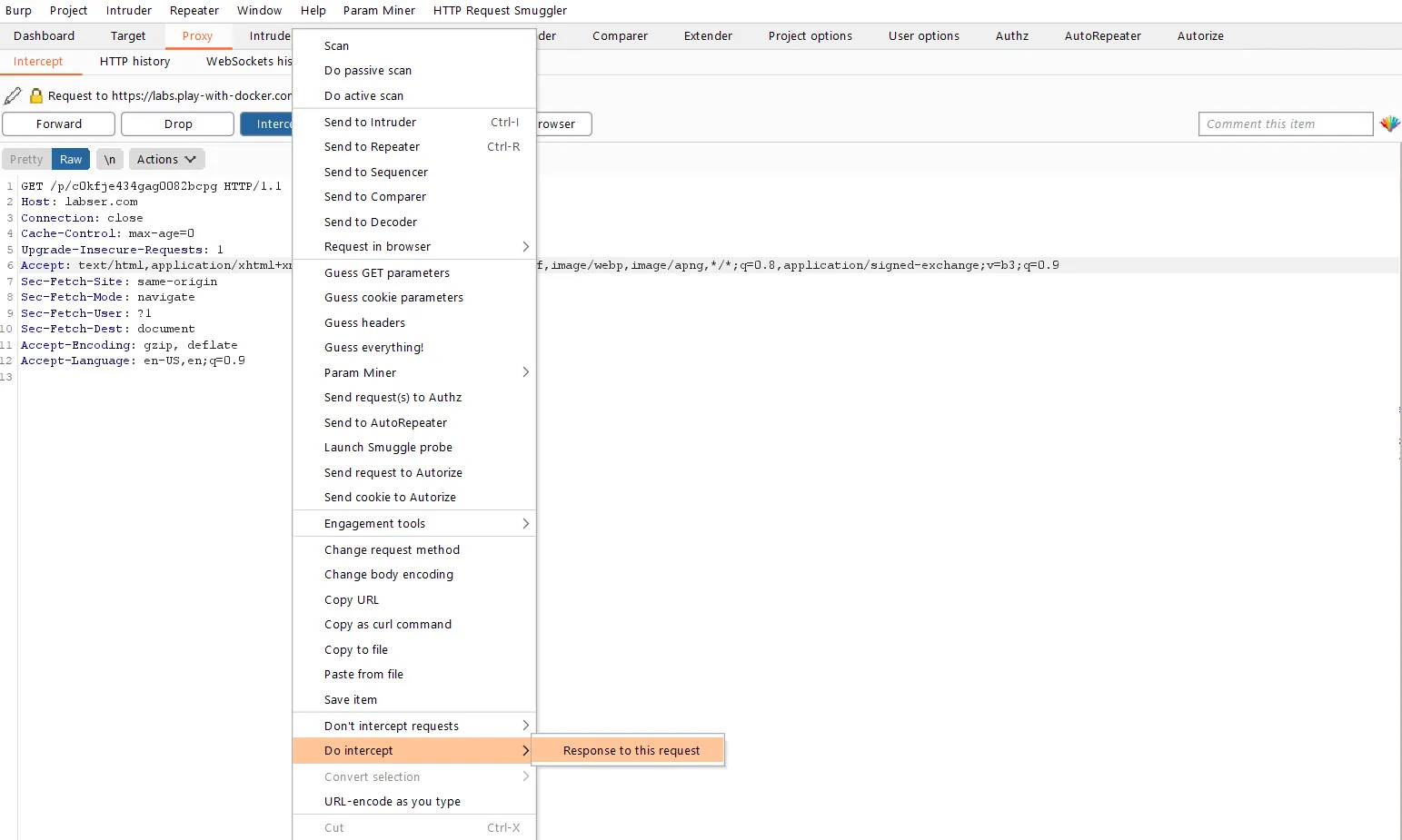
To intercept a Response from a request, one needs to right-click in the Proxy Intercept tab and click on Do intercept > Response to this request from the menu. This instructs the Burp Proxy to intercept the response or data received from the server after the response to the request is forwarded to the server by the Burp Proxy.
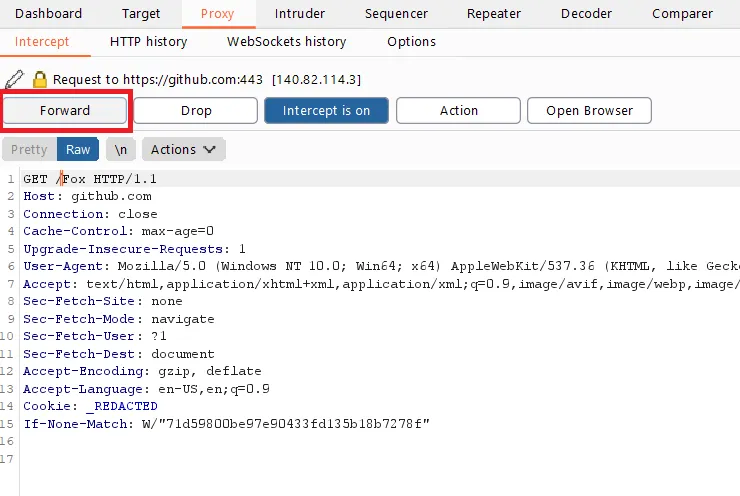
Forwarding Requests Any request sent by the browser can be intercepted in the Proxy Intercept tab. But, to send, or “forward,” the request after it’s intercepted, one needs to click on the Forward button. This allows more control over the requests being sent to the server.
Dropping Requests Proxy also allows to “Drop” or discard, requests that need to be intentionally skipped out or discarded if they are not needed. Requests can also be dropped to check application behavior by blocking a specific request. This can be achieved by clicking on Drop after the request is intercepted.
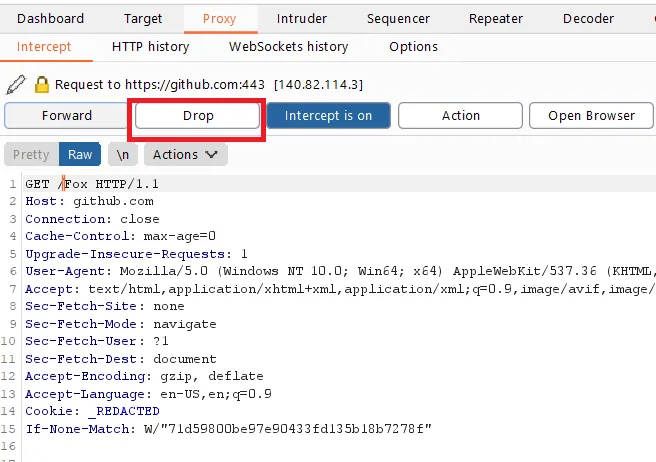
Editing Requests Burp Proxy can edit and modify parts of the HTTP requests before sending them to the server. The Proxy tool works as a live editor to change cookie values or values in the header before forwarding the request. So, one can alter the HTTP requests in real-time to understand how the application behaves and test security flaws. It’s very simple but powerful for application security audits.
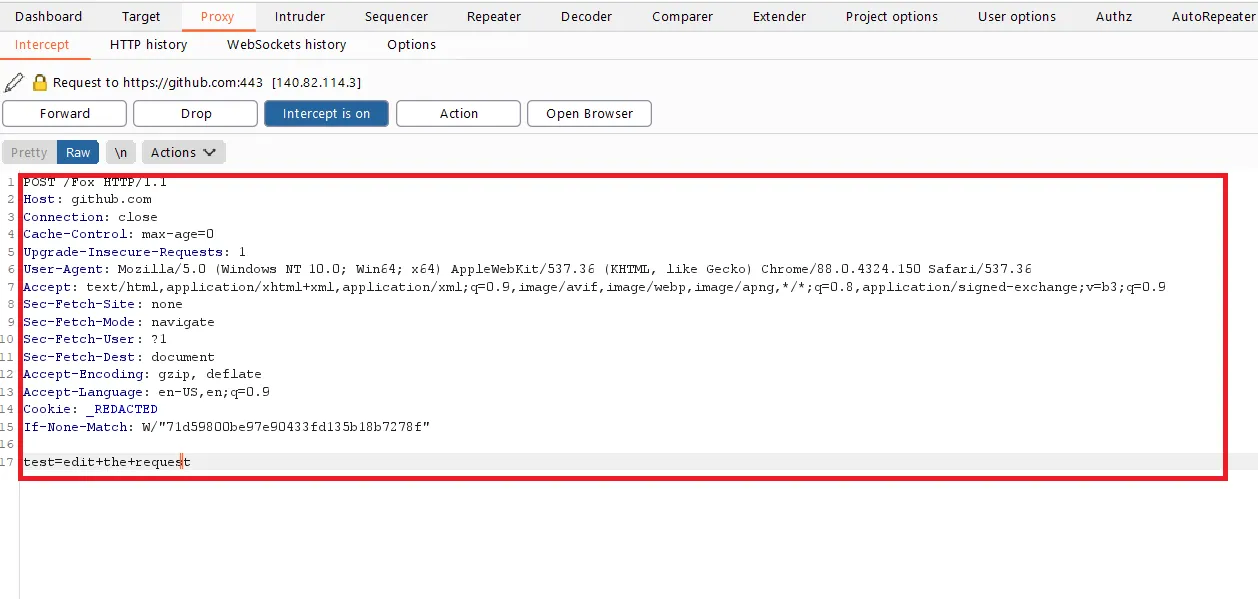
HTTP History Burp Proxy also logs the HTTP requests, and one can quickly check out intercepted requests in the proxy by visiting the HTTP History tab in the Burp proxy. This tab shows a list of requests that passed through the proxy and the respective responses received from the server.
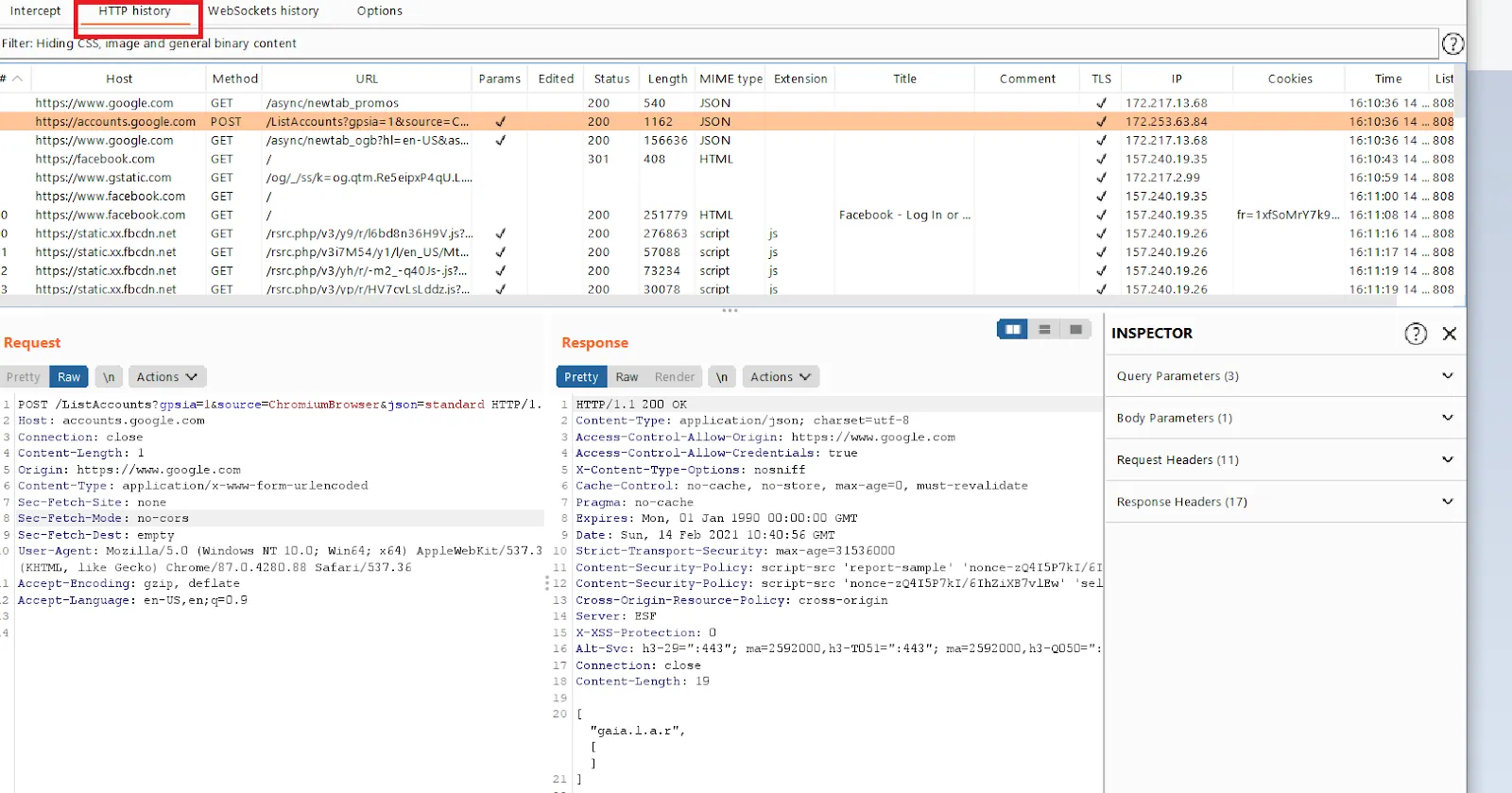
As an analogy, one can consider this similar to browser history. Burp Suite keeps a log of Requests and Responses, which can be later analyzed or retested as needed.
Automatic Response Modification in Burp Proxy
Burp Proxy is quite flexible in terms of options. It offers a very handy Option to enable hidden form fields, enable disabled form inputs, and remove certain hard-coded and client-side limitations. These can be enabled as required. Through such automatic modification of server Response, it becomes easier to check for client-side security control bypasses, and it’s very handy during application security audits. Instead of doing these manually, by enabling these Burp proxy Options, one can save a lot of time during penetration tests.
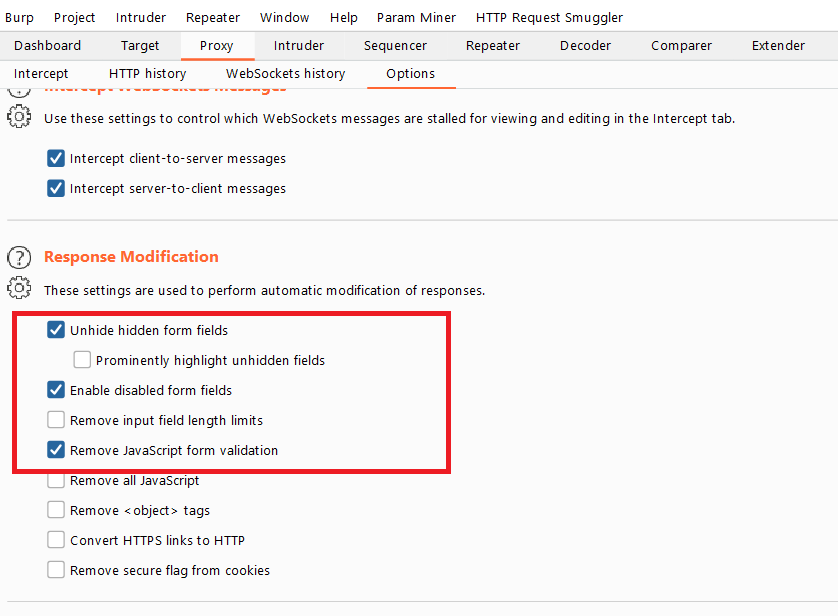
By enabling “Remove Javascript form validation,” it becomes quite easy to test for common business logic flaws within the web app, as developers often implement broken business logic in the backend. An example can be “bypassing the quantity limit and buying items for free” in an e-commerce application. Burp can automatically disable the JS (javascript) based logic and make it easy to find the bug.
Next Steps Burp Proxy is a very useful and powerful feature within Burp Suite. While Burp Suite may seem very complex to the beginner, understanding how to use Burp Proxy and its features in its entirety is essential to perform security audits and penetration tests of web applications. Courses such as those offered by Cybrary can help one get practical hands-on experience in penetration testing with Burp Suite and other industry-leading tools. There are several advanced features in Burp Suite that require dedicated training and professional courses. The Intro to Burp Suite Prois a good way to start learning.





