TL;DR
Introduction
This guide contains the Windows commands most used by attackers as shown by a study of the Japanese National CERT and explains how to defend against these attacks. It also suggests more Windows commands that can also be interesting for potential attackers.
Windows Commands
The most used commands during the attack phases were:
- tasklist. Displays a list of currently running processes on the local computer or on a remote computer.
- ipconfig. Displays all current TCP/IP network configuration values and refreshes Dynamic Host Configuration Protocol (DHCP) and Domain Name System (DNS) settings.
- systeminfo. Displays detailed configuration information about a computer and its operating system
- netstat. Displays active TCP connections, ports on which the computer is listening, Ethernet statistics, the IP routing table, IPv4 statistics (for the IP, ICMP, TCP, and UDP protocols), and IPv6 statistics
- whoami. Displays user, group and privileges information for the user who is currently logged on to the local system.
- qprocess. Displays information about processes that are running on a Remote Desktop Session Host (RD Session Host) server.
- query. Displays information about processes, sessions, and Remote Desktop Session Host (RD Session Host) servers.
- net. Used to perform operations on Groups, users, account policies, shares etc.
- at. Schedules commands and programs to run on a computer at a specified time and date.
- reg. Performs operations on registry subkey information and values in registry entries.
- wmic. Command-line and scripting interface that simplifies the use of Windows Management Instrumentation (WMI) and systems managed through WMI.
- wusa. Uses the Windows Update Agent API to install update packages.
- netsh. Command-line scripting utility that allows you to, either locally or remotely, display or modify the network configuration of a currently running computer.
- sc. Communicates with the Service Controller and installed services.
- rundll32. Loads and runs 32-bit dynamic-link libraries (DLLs).
The following commands are not mentioned in the article, but they could be included in the block list due to their features:
- quser. Displays information about user sessions on a Remote Desktop Session Host (RD Session Host) server.
- qappsrv. Displays a list of all Remote Desktop Session Host (RD Session Host) servers on the network.
- qwinsta. Displays information about sessions on a Remote Desktop Session Host (RD Session Host) server.
- taskkill. Ends one or more tasks or processes. Processes can be ended by process ID or image name.
- regedit. Utility for editing the registry.
- regedt32. Utility for editing the registry.
- regsvr32. Registers .dll files as command components in the registry.
- regini. Modifies the registry from the command line or a script, and applies changes that were pre-set in one or more text files.
- telnet. Communicates with a computer running the Telnet Server service.
- tftp. Transfers files to and from a remote computer that is running the Trivial File Transfer Protocol (TFTP)
- tracert. Determines the path taken to a destination by sending Internet Control Message Protocol (ICMP) Echo Request or ICMPv6 messages to the destination with incrementally increasing Time to Live (TTL) field values.
AppLocker AppLocker is a feature in Windows Server 2012, Windows Server 2008 R2, Windows 8, and Windows 7 that advances the functionality of the Software Restriction Policies feature. AppLocker helps administrators control how users can access and use files, such as executable files, scripts, Windows Installer files, and DLLs.The software restriction policy of AppLocker allows you to limit the capabilities of the attacker.In order to configure AppLocker, launch gpedit.msc and go to Local Computer Policy > Computer Configuration > Windows Settings > Security Settings > Application Control Policies > AppLocker.
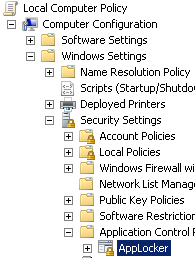
Now, we can add the commands we want to deny under Executable Rules. If we want to apply the rules to de Administrators Group, delete the BUILTINAdministrator rule.
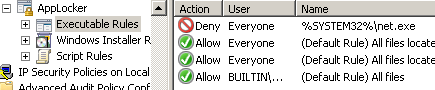
Enable the Executable rules under AppLocker properties.
The AppLocker depends on the Application Identity Service. Launch services.msc and set it to Automatic startup or the rules will not be enforced.

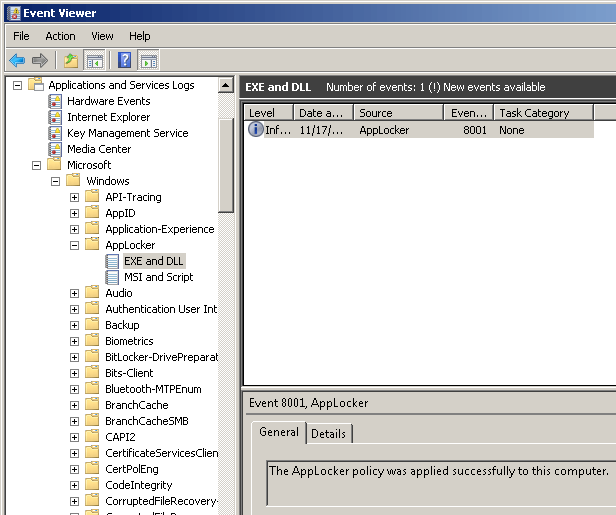
We can check the logs of AppLocker in Applications and Services Logs > Microsoft > Windows > AppLocker.
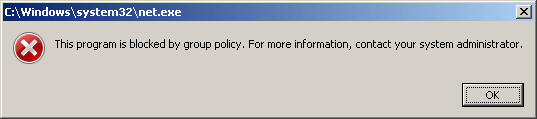
Now, if an unauthorized user tries to launch a denied command, he will receive a warning message and the attempt will be logged.
Conclusion
AppLocker is a simple and effective way to restrict the capabilities of the attackers on Windows environments provided by Microsoft. Nevertheless, it does not work if the attackers download third party tools.A more extreme solution is to delete any unneeded executable. But this option is more difficult to revert and can lead to system instability.





