TL;DR

Introduction
Socat is a multi-purpose networking tool which can be used to accomplish various networking tasks (refer to SOCAT as a Polymorphic Networking Tool which gives an overview on the many uses of Socat). In this article, Socat will be used to setup an SSL VPN tunnel between two endpoints, which could be separated over a large distance. Firstly, the creation of client/server private keys and certificates will be covered, which are required to encrypt the VPN tunnel. The necessary Socat commands will then be covered to setup the VPN tunnel. Allowing remote access to the VPN server will be discussed, along with the necessary configurations needed to allow remote access to the local network.
OpenSSL Client/Server Configuration
Client/server private keys and certificates will firstly need to be created to later assist with encrypting the VPN tunnel.
Server configuration:
1. Create the private key:
openssl genrsa -out server.key
2. Create the self-signed certificate:
openssl req -new -key server.key -x509 -days 365 -out server.crt
3. The above command will ask you to fill in the certificate information. Follow the prompts.
4. A PEM file is also required for Socat and is created as follows:
cat server.key server.crt > server.pem
5. Ensure that the private key and PEM file are only readable and writable by the owner:
chmod 600 server.key server.pem
6. Copy the server.crt over to the client.
Client configuration:
Repeat steps 1-5 above, substituting server for client. Copy the client.crt over to the server. Next, the creation of the SSL VPN will be covered.
Creating the SSL VPN
Two commands are required to setup the secured tunnel between the two endpoints, one on the server and the other on the client.
VPN Server:
sudo socat -d -d OPENSSL-LISTEN:4443,cert=server.pem,cafile=client.crt,reuseaddr,fork TUN:10.2.0.1/24,up
The above command sets up an OpenSSL listener on port 4443. When a connection is received on port 4443, a TUN (TUNnel) interface with the 10.2.0.1 address is enabled. The -d -d flags print extra messages to the terminal. cert= points to the server.pem file containing the server's private key and certificate. cafile= points to client.crt, the client's certificate. The reuseaddr option will allow the VPN server to be kept in a listening state. The fork option allows the VPN server to handle multiple connections.
VPN Client:
sudo socat -d -d OPENSSL:192.168.2.10:4443,cert=client.pem,cafile=server.crt TUN:10.2.0.2/24,up
In the above command, 192.168.2.10 refers to the VPN server where the socat instance is listening for connections. Running the command will establish an SSL connection with the VPN server and a TUN interface with the 10.2.0.2 address will be enabled for the client. The VPN connection can be tested by opening another terminal and pinging the 10.2.0.1 IP address of the VPN server from the client. Allowing remote access to the VPN server will be discussed next.
Allowing Remote Access
The VPN setup can be extended to allow remote access to the VPN server over the internet. To do this, a port forwarding rule on the VPN server's router will need to be added. This will map the VPN server's IP address and port (192.168.2.10:4443) to the public IP address of the router and port 4443.With the current setup, the VPN client should only be able to access the 10.2.0.0/24 TUN network. In order to access the devices on the 192.168.2.0/24 local network, two static routes will need to be added: a static route pointing the VPN client to the local network, added on the VPN client and a static route for the return traffic pointing to the VPN TUN network, added on the router. IP forwarding will also need to be configured on the VPN server.
Enabling IP Forwarding
To enable IP forwarding, run the following command as root:
echo 1 > /proc/sys/net/ipv4/ip_forward
The last step to allow access to the local network via static routes will be covered below.
Adding Static Routes
On the VPN client, enter the following command which will create a static route to the local network via the VPN server:
sudo route add -net 192.168.2.0 netmask 255.255.255.0 gw 10.2.0.1
The argument to -net is the local network address, netmask is the subnet mask of the local network and the argument to gw is the TUN IP address of the VPN server, which the traffic will pass through in order to reach the local network.To allow the VPN client to receive return traffic from devices on the local network, a static route will need to be created on the router (192.168.2.1) which points to the VPN TUN network via the VPN LAN server IP 192.168.2.10. The static route parameters are specified below and not the command, as the syntax of the command will depend on the type of router used.
network: 10.2.0.0, netmask: 255.255.255.0, gateway: 192.168.2.10
In addition, firewall rules may need to be added to the VPN server, in order to allow traffic to be forwarded to the internal LAN. Firewall rules may also need to be configured on the LAN clients, in order for them to be accessed by the VPN client.The below figure depicts a Socat SSL VPN tunnel which has been set up between two remote locations. Once IP forwarding is enabled and the above static routes are added, the remote VPN client will be able to access the 192.168.2.0/24 LAN of the VPN server.
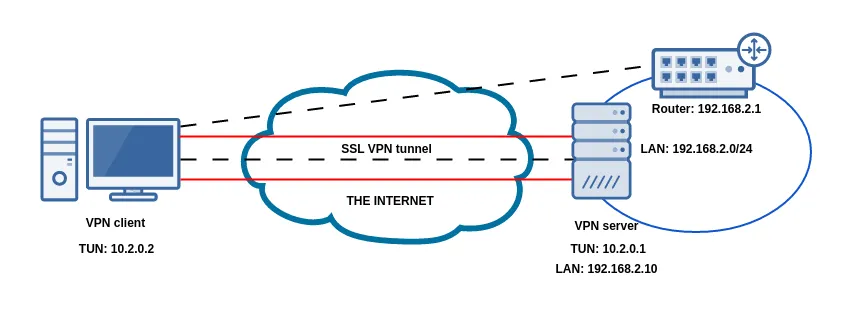
Figure 1: Socat SSL VPN tunnel setup between two remote endpoints
Conclusion
Creating an SSL VPN connection between two endpoints can easily be done using Socat. Before the VPN is launched, OpenSSL client/server keys and certificates need to be created in order to secure the connection. Once these files are created, the VPN server and client can be created using two commands. The Socat SSL VPN can also be used between two remote endpoints, but additional configuration is needed to enable port forwarding. In addition to enabling a port forwarding rule, IP forwarding and static routes need to configured in order to allow remote access to the local network.
References
- https://www.dest-unreach.org/socat/doc/socat-openssltunnel.html
- http://www.dest-unreach.org/socat/doc/socat-tun.html
- https://linuxconfig.org/how-to-turn-on-off-ip-forwarding-in-linux
- http://www.networkinghowtos.com/howto/adding-a-static-route-in-linux/





