How to Make the Most of Blending Learning with Cybrary Live
Learn how to get the most from your cybersecurity training platform by blending on-demand learning with virtual, live courses led by industry experts.
Cybrary's accessible, affordable training platform provides curated career paths, threat-informed training, and certification preparation for professionals at all levels.


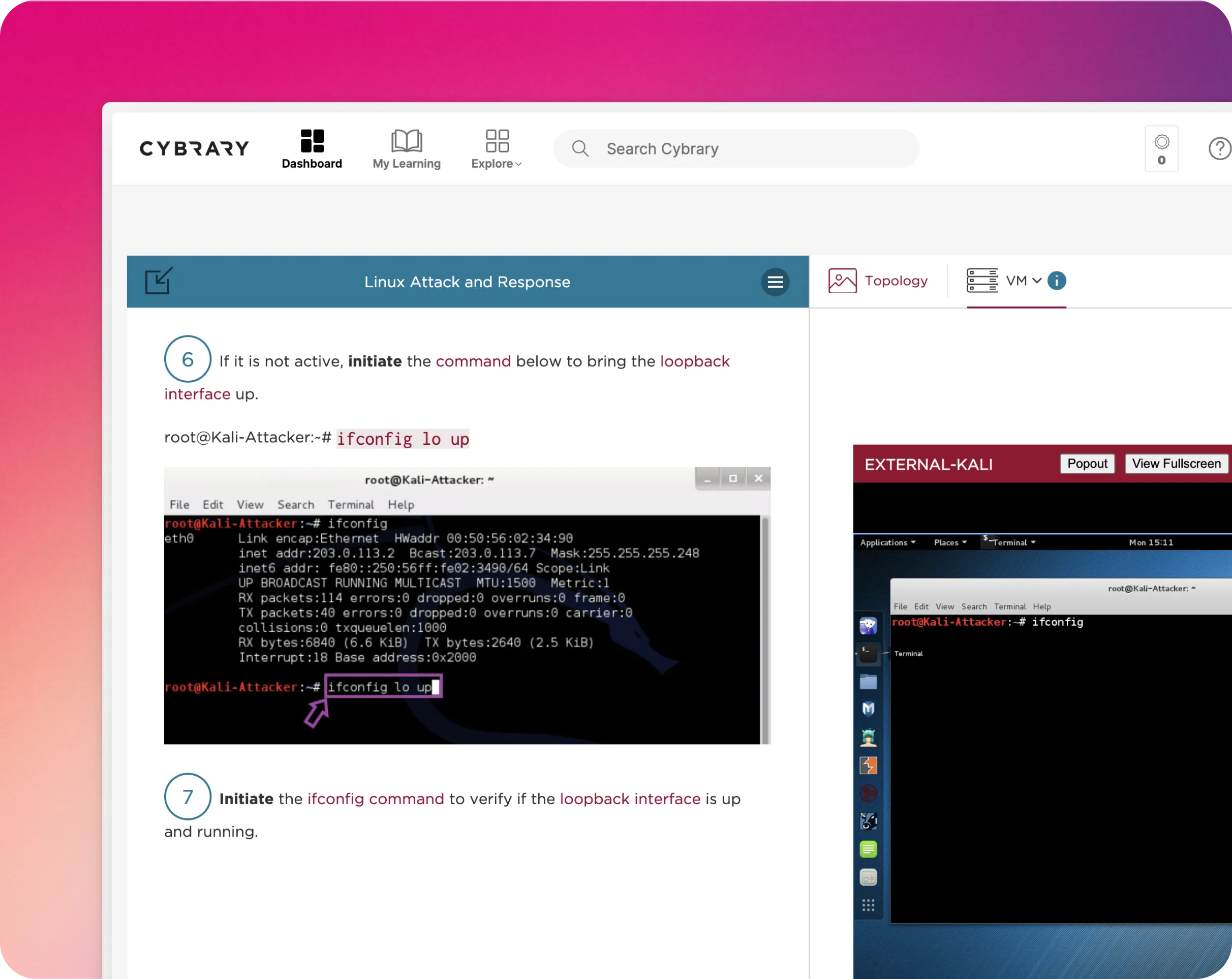
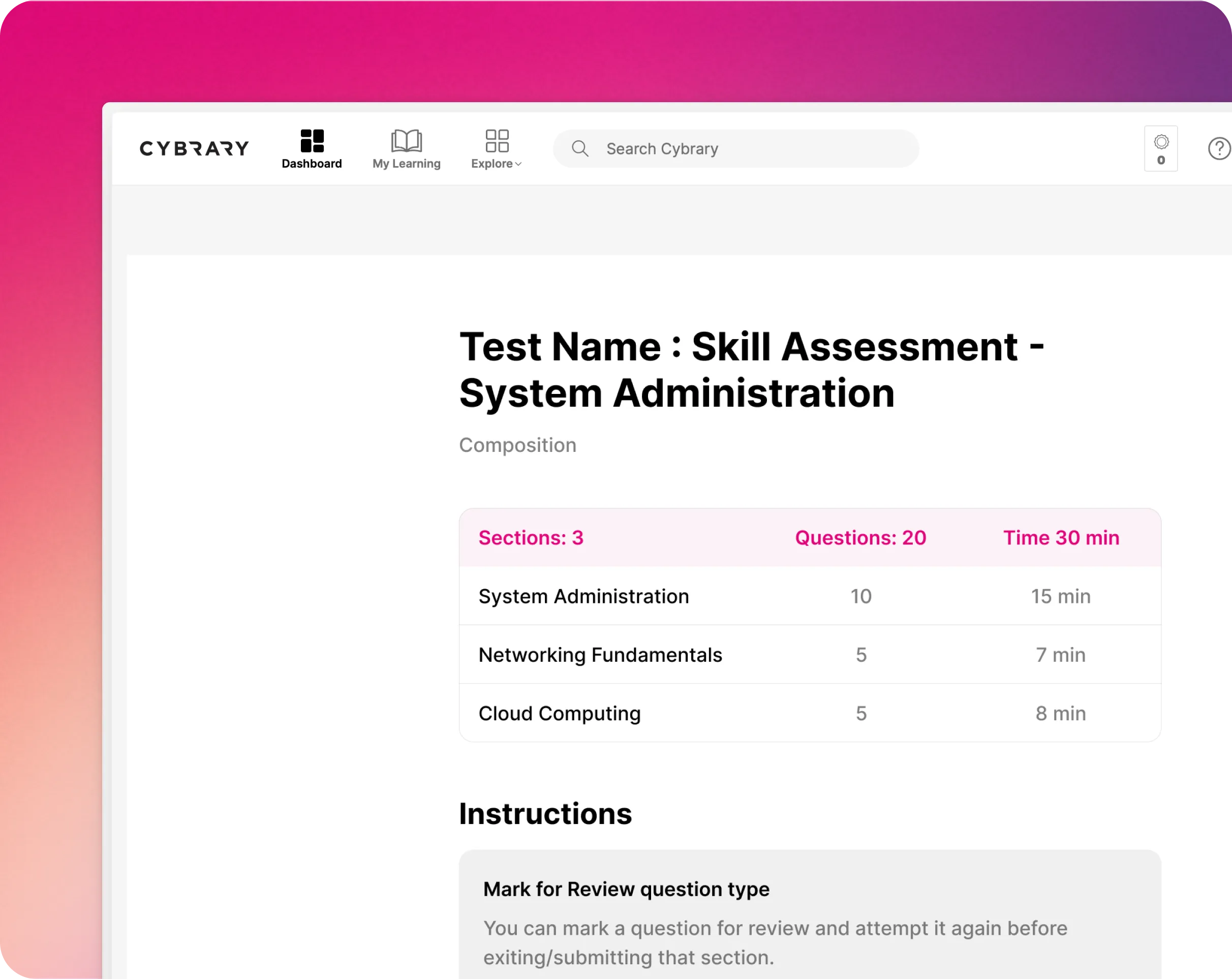
Upskill your team with Cybrary's suite of learning activities and management tools, including hands-on practice labs, assessments, and custom guided pathways. Request a demo and learn how Cybrary tailors our deep library of trainings to your team's unique needs.





















































































Explore our on-demand courses developed by seasoned certified cybersecurity practitioners, aligned to the certification exam’s key learning objectives.